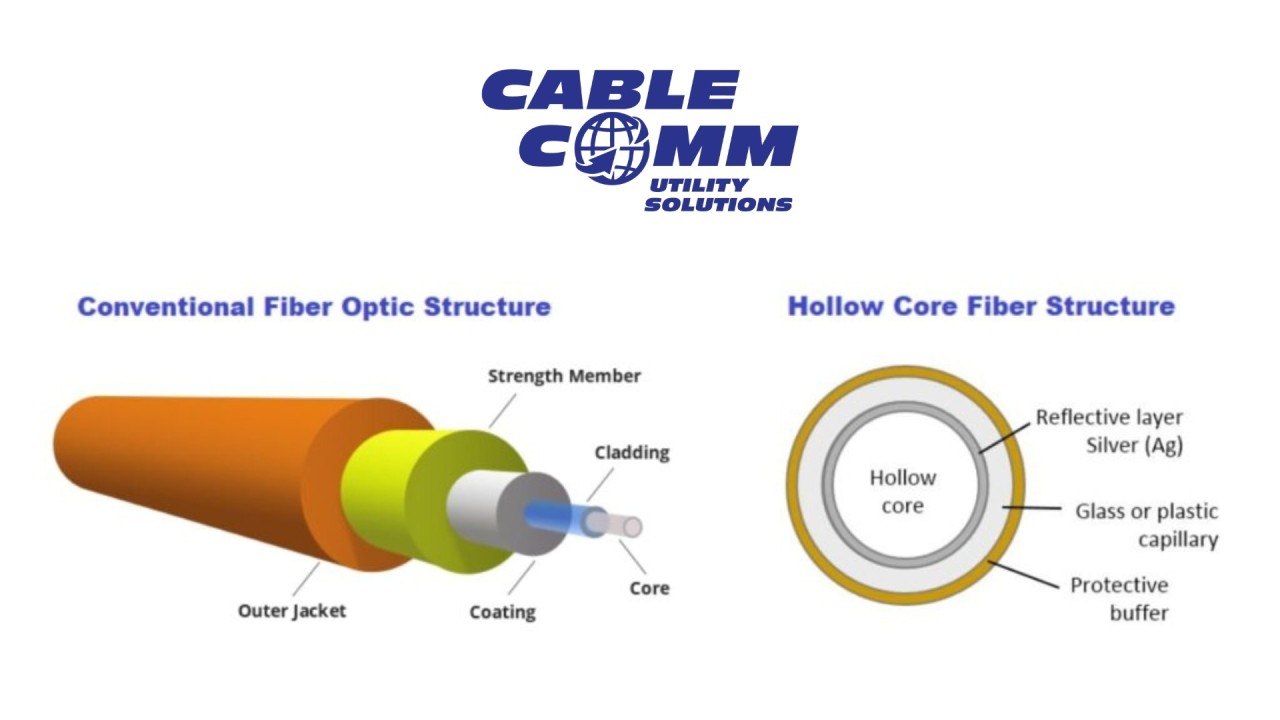
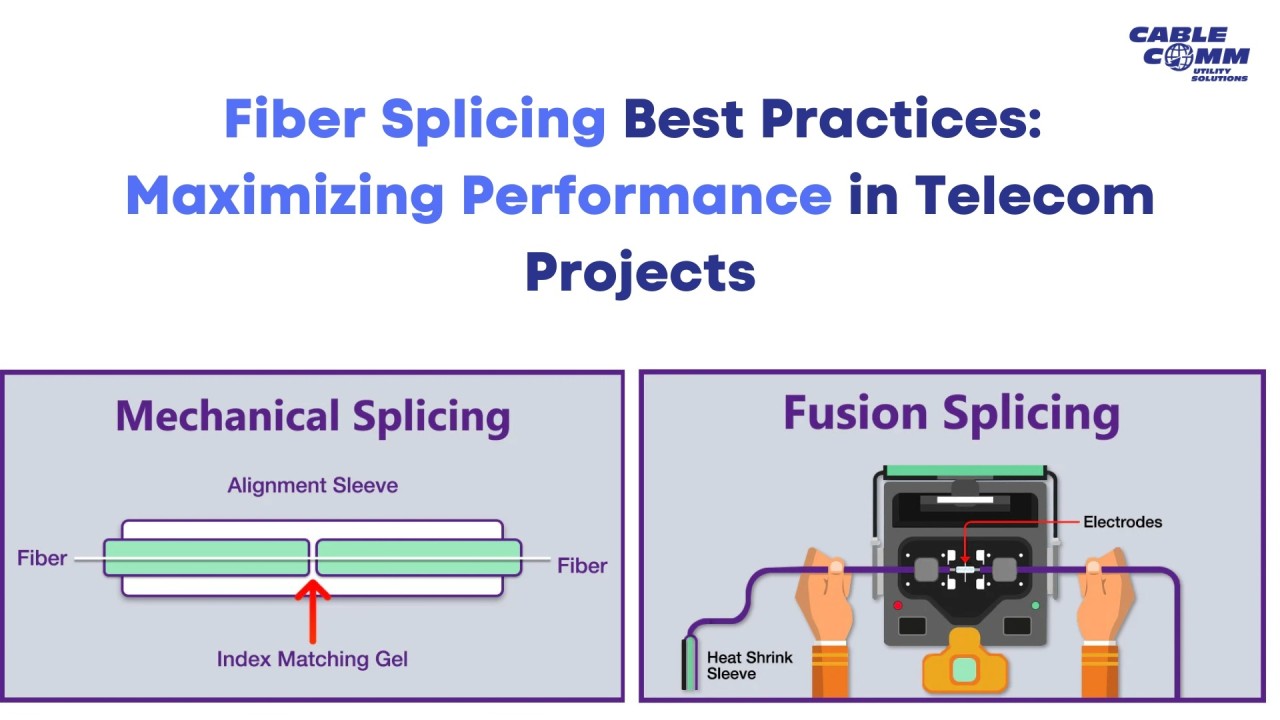
In this day and age of interconnectivity fueling innovation, ensuring the security of telecommunications networks has become integral to success. But with billions of devices connected over networks that span the globe and the arrival of technologies like 5G and IoT, the telecom industry faces new challenges to keep its infrastructure secure. But emerging telecom security trends are creating a path toward a secure, resilient future.
Cyber Threat Landscape Surge
In the past year, there has been an uptick in telecom network attacks that are hitting as cyber threat actors. As Nokia reported in 2022, telecom networks experienced a 70% increase of malware over the year before. Whether ranging from Ransomware to Distributed Deny of Service (DDoS) it has the same effect of stopping services for millions of users, stealing data that hackers can never determine or losing trust.
‘The most important target for cybercriminals today is the ‘nerve center’ of the digital economy — the telecom network,” states John Anderson, Cybersecurity Consultant with Palo Alto Networks.
Current developments on telecom security and privacy issues
Zero Trust Architecture( ZTA):
There is no such thing as Perimeter-Based Security Any More In The Era Of Threats. In contrast, Zero trust confirms that every user and device must be authenticated before one can access the network so the risk of a breach to the host altogether is significantly degraded. Globally, 60% of enterprises will use Zero Trust by 2025, as Gartner foresees – the cornerstone of telecom security.

AI-Powered Threat Detection:
Artificial intelligence is changing how vulnerabilities are identified and mitigated. Machine learning analyzes very large data streams from a network in its real-time, catching any differences that signal an approaching attack. AT&T found it could decrease threat response times by 35% after cyber security enterprise integration with AI-driven security tools.
Quantum-Resistant Cryptography:
Current encryption methods will soon be obsolete with the arrival of quantum computing. To help protect telecom data against this nascent threat, quantum-resistant algorithms are being designed every next year the USTR will formally publish a list, published as quantitative criteria in a sweeping new presidential document about quantum computing that rolled out last month it must include quantum secure cryptographic and other post-quantum.
Security Protocols for 5G
With the move to 5G there are additional unknowns, i.e. a larger attack surface due to network slicing and edge computing. The Telecom Infra Project (TIP) drives the standardization of 5G security, such as improved encryption and secure APIs.
The Role of Collaboration
But telecom network security can not be a one-person game. Industry collaboration is crucial to combat the ever evolving threats. For example, the GSMA and CISA (Cybersecurity and Infrastructure Security Agency) are bringing telco operators together with governments and cybersecurity vendors to share insights, build joined-up strategies.
“Collaboration is the only way to achieve telecom security, says Lisa Rodriguez, Director of Cyber Strategy at GSMA. “No single entity can address these challenges alone”.
Secure Infrastructure commitment of Cable Comm
We know at Cable Comm, relying on reliable infrastructure is the cornerstone of good security. Our infrastructure is secure from the deployment of fiber optics all the way to having advanced monitoring systems integrated into every single project we do. Staying updated with the newest in operating security advancements gives clients a network that has all facilities for present upload, and 11 years tomorrow.
Conclusion
Telecom security looks to be a battle ridden, yet promising future. Cyber threats are getting more stealthy, which means we are encouraged to be equipped with the tools and methods needed to defend against them. The road to innovation is literally measured in seconds for telecom execs; standing on the downhill end of new AI methods, Zero Trust implementation and quantum-resistant encryption are fun but collaboration must happen organically across all parts of industry.
As we move into this hyper-connected volley networks secure are not enough-they should be the very core of progress. Join us in making this happen, a more resilient telecom future.
Can your networks handle the security of tomorrow? Reach out to Cable Comm for ways we can help you defend infrastructure from new threats.